Screen Watermark & Anti-Screenshot
xSecuritas Screen Watermark is an enterprise screen watermark and anti-screenshot solution that overlays visible and invisible watermarks, blocks screen capture tools and camera-based capture, and integrates with Microsoft Sensitivity Labels and Active Directory on Windows, macOS, Linux and Android.
By using the xSecuritas Screen Watermark product, you can prevent users from leaking information on the
screen by taking screenshots or capturing the screen with a camera. Screen Watermark provides both visible
watermarks that appear only when needed and invisible watermarks that minimize user inconvenience while
still providing strong traceability for security teams.
The solution supports more than 30 types of meta-text, including user ID, IP address, MAC address, date
and time, Active Directory information, and Microsoft Sensitivity Labels (Data Classification). These
values can be displayed or embedded as watermarks. Policies are created easily on a web-based policy
server with an intuitive UI and can be linked directly to Active Directory users or groups for
organization-wide consistency.
Screen Watermark also works in virtual and remote environments such as VDI, RemoteApp and remote desktop,
and it can display watermarks even when an agent is not installed on the endpoint device. When the user
shares their screen in video conferencing tools such as Microsoft Teams, Zoom or Cisco WebEx, the
watermark appears on participants’ screens, and optional webcam watermarks can be applied to video feeds.
xSecuritas products are already used reliably by more than 350,000 users worldwide. Screen Watermark is
available as both a cloud service and a fully on-premise edition; the on-premise version does not require
any Internet access and is suitable for high-security environments such as government, banking and
defense. Please request a trial and experience how xSecuritas Screen Watermark can protect your screens
and prevent data leakage.
How xSecuritas Screen Watermark Enterprise Works
Architecture Overview (Agent ↔ Policy Server)
Agent (Windows / macOS / Linux / VDI Host)
Identifies device/user attributes (User ID, Hostname, AD attributes, IP/Subnet, Microsoft Sensitivity Label, etc.)
Generates the watermark overlay using GPU or OS-level rendering layers
Retrieves the latest policy from the Policy Server using a secure pull model
Detects screenshot, print, and webcam access events
Encrypts and uploads security events and forensic logs to the Policy Server
Policy Server (Cloud or On-Premise)
Maps policies by AD OU, user, group, domain, or IP address
Manages watermark templates, metadata rules, and environment logic
Tracks Agent status and supports remote quit/uninstall
Stores logs, forensic data, and audit records in centralized storage
Workflow on Local PC or VDI Host
The user installs the Agent (or it is auto-launched on a VDI host)
The Agent registers with the Policy Server and downloads the assigned policy
Each policy contains display text, transparency, repetition pattern, QR/image options, colors, position mapping, and Sensitivity Label rules
The Agent analyzes OS resolution, multi-monitor layout, and DPI scaling to render the watermark at optimal coordinates
If the network is interrupted, the Agent continues operating using the last cached policy (offline fail-safe mode)
Screenshot actions (Win+Shift+S, PrtScn, Snipping Tool), print jobs, or webcam usage events are detected and logged
Logs are sent to the server immediately or in scheduled batches based on configuration
Administrators can view watermark status, device connections, and security events per user or machine
Workflow for RemoteApp / XenApp / Horizon / Frame
The Agent is installed only on the RemoteApp/XenApp server, not on the user’s PC
When a user opens Word/Excel/Browser inside the RemoteApp session, the watermark overlay is rendered inside the virtual window
Watermarks appear consistently even if the user’s endpoint does not have the Agent installed
Policy Server automatically assigns watermark policies based on domain, IP, OU, or user identity
Screenshot permissions are evaluated based on server-side rules and client communication
Invisible Watermark is automatically embedded in captured images even in RemoteApp sessions
Environment-Aware Policy Logic
Corporate network vs external network → watermark mode switches automatically
ICMP/Ping availability is used to detect office vs remote conditions
IP/Subnet changes trigger policy reassignment or text/metadata adjustments
AD security group changes dynamically update corresponding watermark policies
System differentiates between Remote Desktop vs Local Desktop automatically
Security, Logging & Compliance Engine
Screenshot, print, and webcam events are locally encrypted before transmission
The server correlates events with AD identity, session ID, and assigned policies
Administrators filter logs by time, device, application, process, and policy
Invisible forensic watermark embeds a unique correlation code inside captured images
Even if a screenshot leaks externally, the server can trace the exact user and device
High-Availability & Fail-Safe Mode
If Agent loses connection to the server, cached policies remain active
Watermarks continue to display without interruption
Once the server becomes available, the Agent automatically resynchronizes
Remote uninstall/quit commands are queued and executed after reconnection
Policy Server Controls
When an admin saves a policy, all Agents update automatically based on their polling interval
Multiple policies can be created for departments, groups, users, or IP ranges
Administrators can remotely terminate or uninstall Agents
Real-time monitoring shows Agent connection status, active policies, and version info
Event logs (screenshot, print, webcam) are centralized and searchable in the Policy Server
Agent Installation, Auto-Update & Remote Removal
Automated Agent Updates (Windows / macOS / Linux)
Enterprise Deployment via SCCM / MDM
Remote Removal & Bulk Uninstallation
Product Details
Supports 4 types of watermark display
-
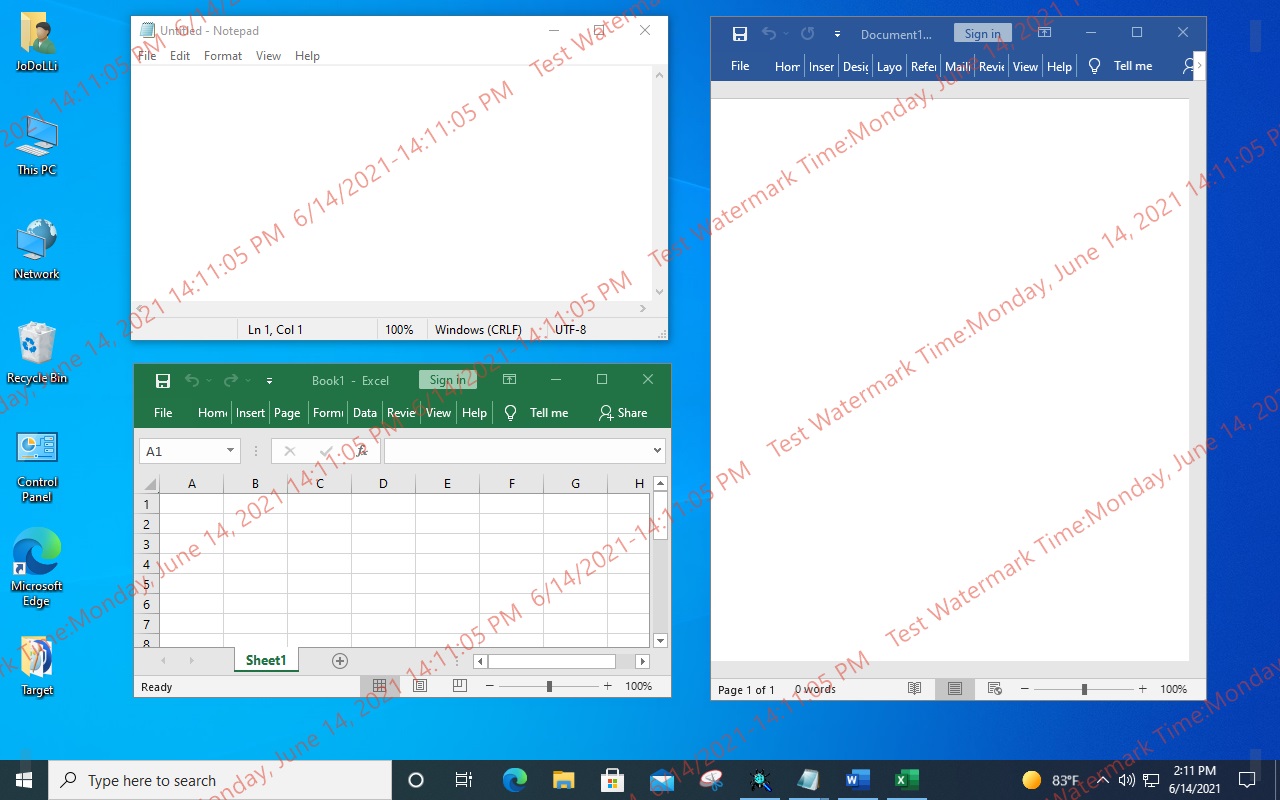
The watermark is displayed on all monitors or only some monitors. -
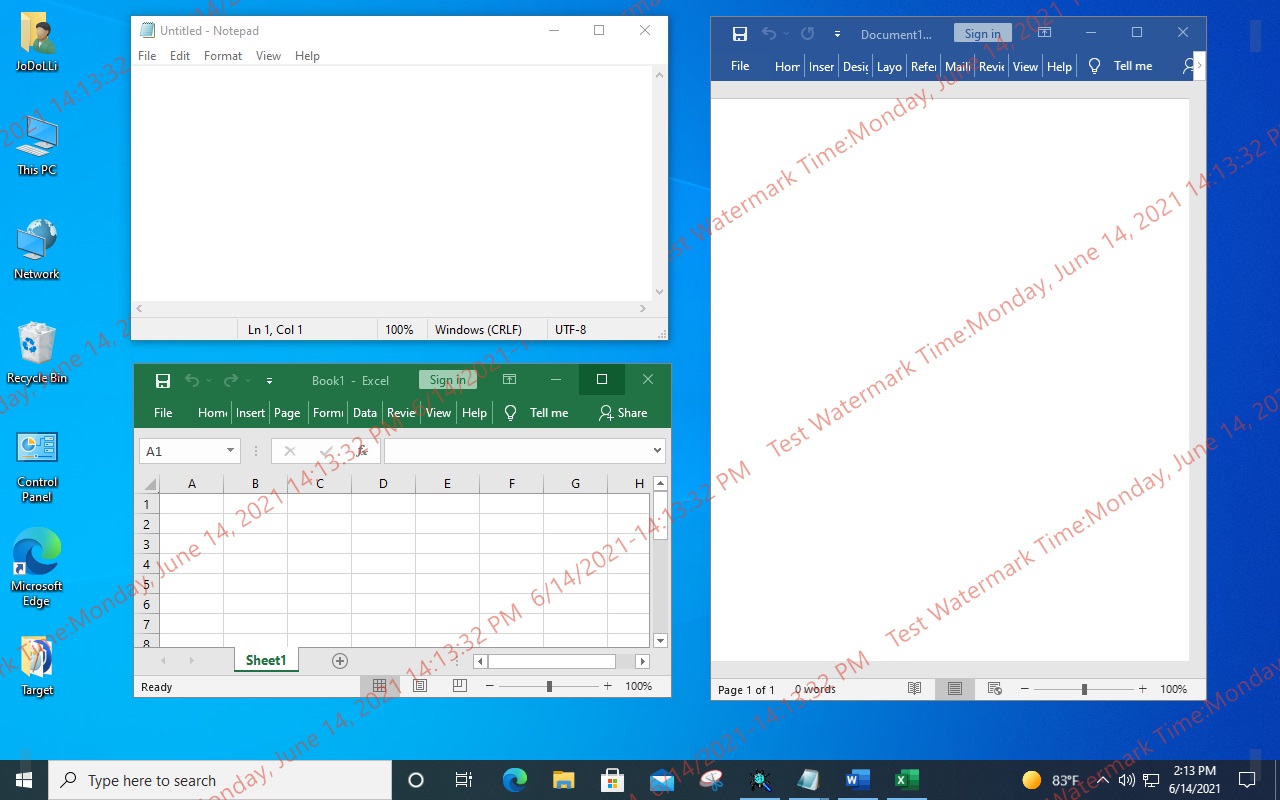
The watermark is displayed on the desktop and in each window. -
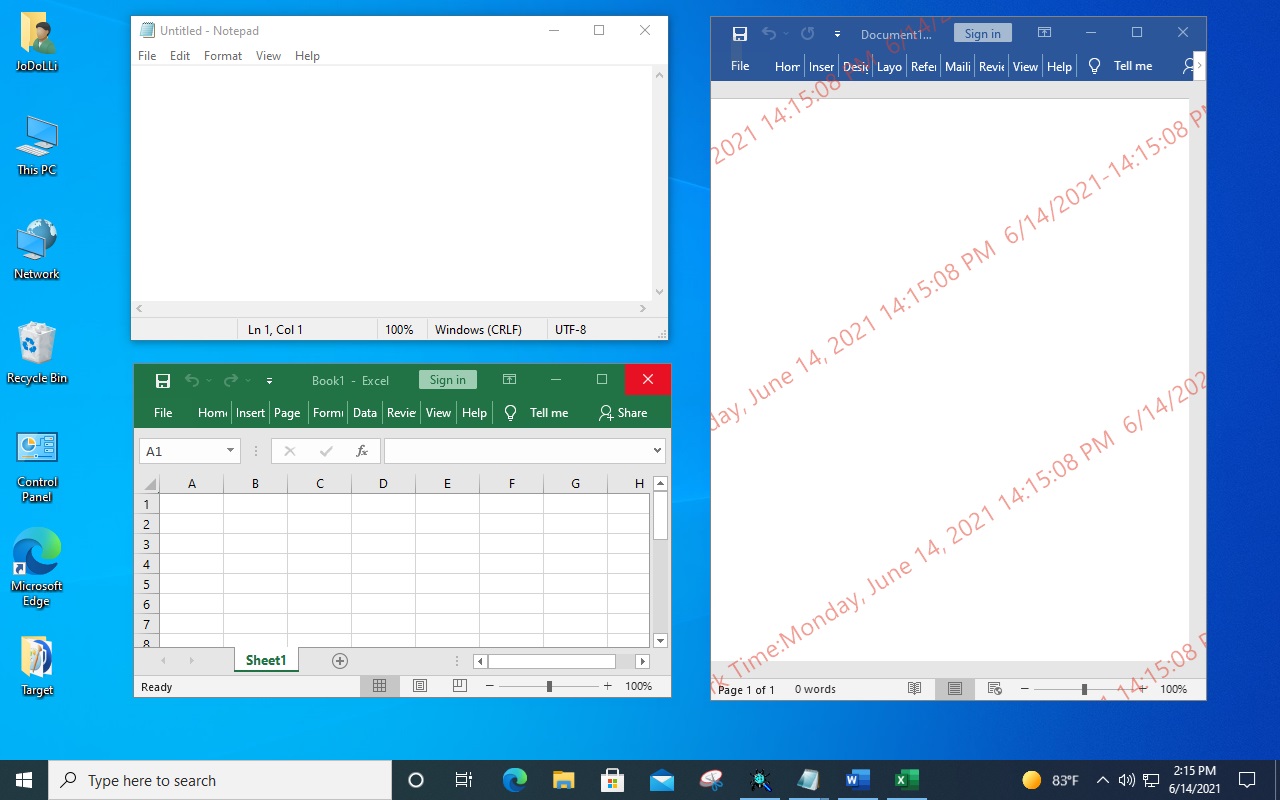
The watermark is displayed only on the specified applications and websites. -

The watermark is not displayed neither only on the specified applications nor websites.
VDI & REMOTEAPP support
When using RemoteApp, xenApp or Remote Desktop, the watermark is displayed even without installing an agent on the user's PC.
Supported Applications: Microsoft RDS, RemoteApp, Citrix, VMWare Horizon, AWS Stream, Dizzion Frame, etc.
-
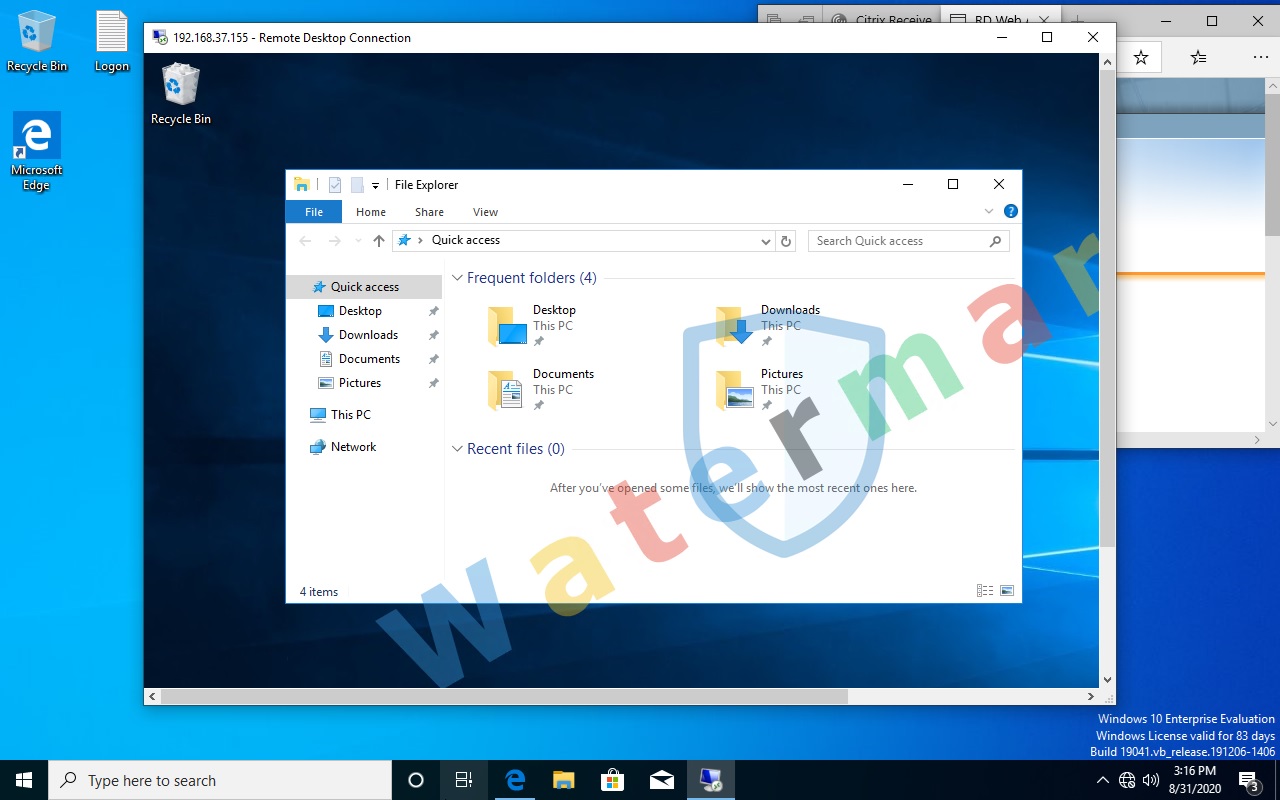
When using remote desktop -

When using Remote App, xenApp, etc.
Support for displaying sensitivity labels (Data Classification) as watermarks in Office 365, SharePoint
Depending on the sensitivity label (Data Classification), you can show or hide the watermark.
The watermark can be displayed only on documents with the specified sensitivity labels.
Supports OneDrive and SharePoint.
-

Watermark displayed in Office 365 -

Watermark displayed in SharePoint
Video conferencing tool support
When you share your entire screen or specific content using a video conferencing tools such as ZOOM, Microsoft Teams, or WebEx, the watermark appears on participants' screens.
When video conferencing using a webcam, you can display a webcam watermark on the host and participant video screens.
Supported Applications: Microsoft Teams, CISCO WebEx, ZOOM
-

Even if you share some contents only, a watermark will appear on participant screens. -
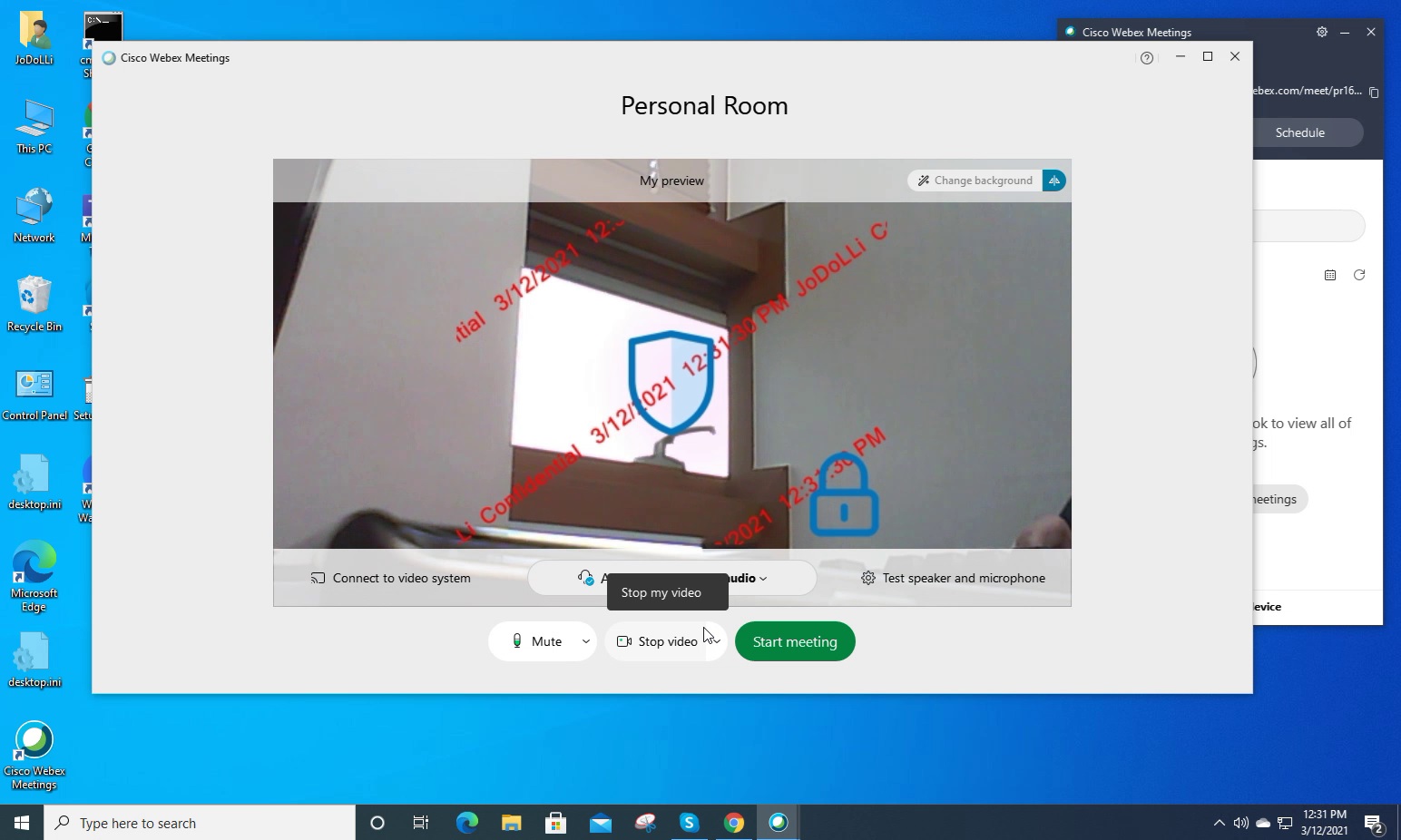
When you use the webcam watermark feature, a watermark will appear on the video screen.
Invisible watermark
When you capture the screen, an invisible watermark is included in the captured image.
And this is not visible to the user, but administrator can extract information from the invisible watermarks using a dedicated program.
-

Captured image (invisible watermark included) -
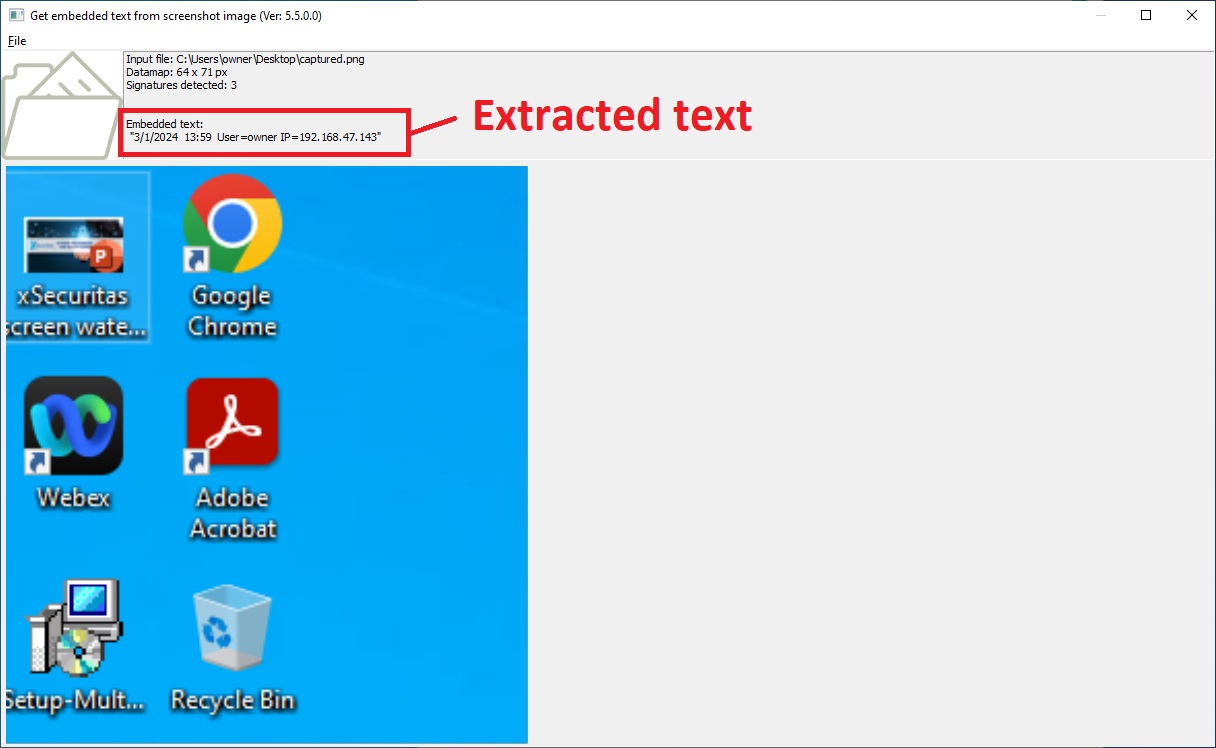
You can extract information from invisible watermarks using a dedicated program.
Screen capture prevention function
Prevents capturing the entire screen.
Controls the specified application window from being captured.
When a user captures the screen, the captured image can be saved on the server or emailed to the administrator.
-
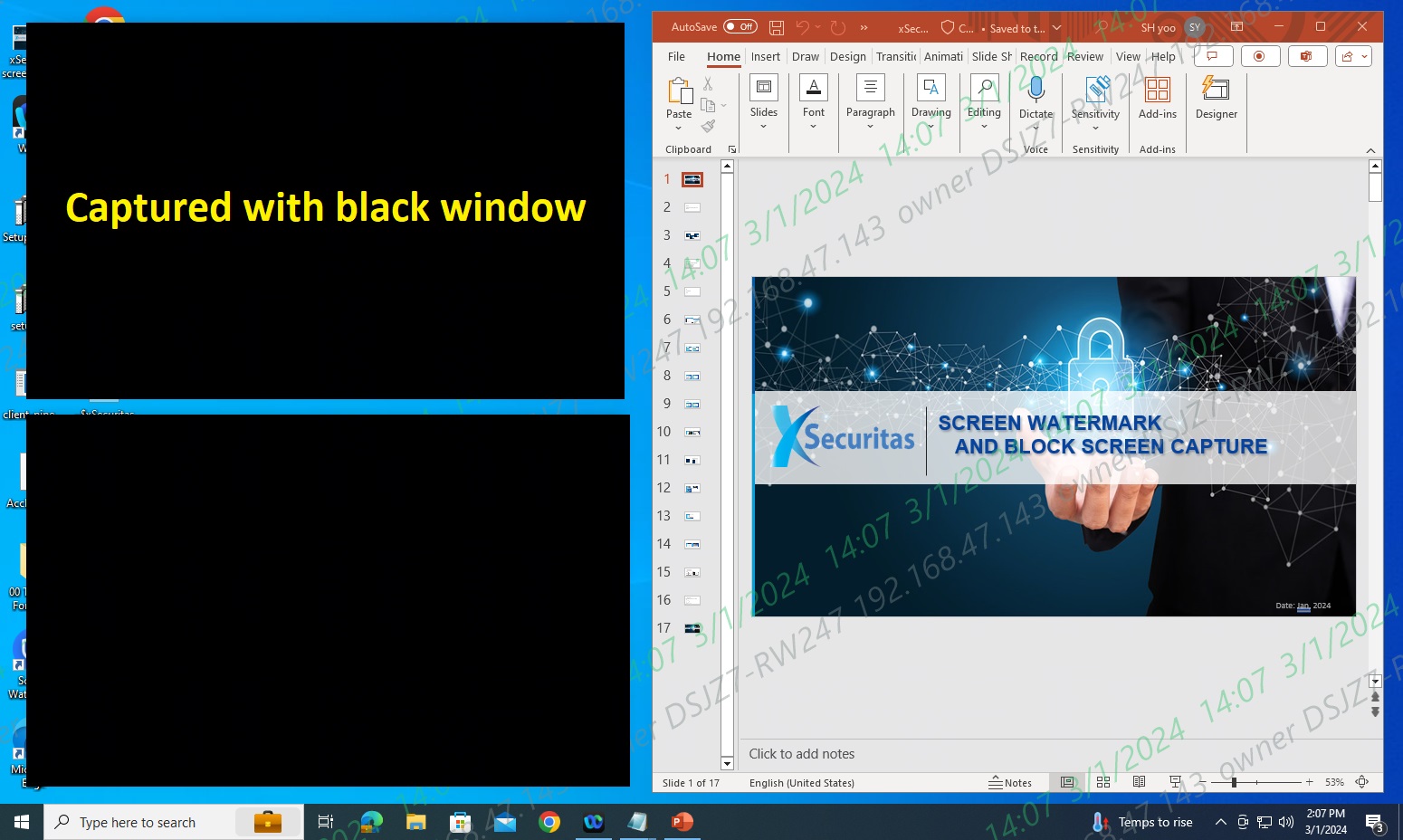
Block capture of only some windows -
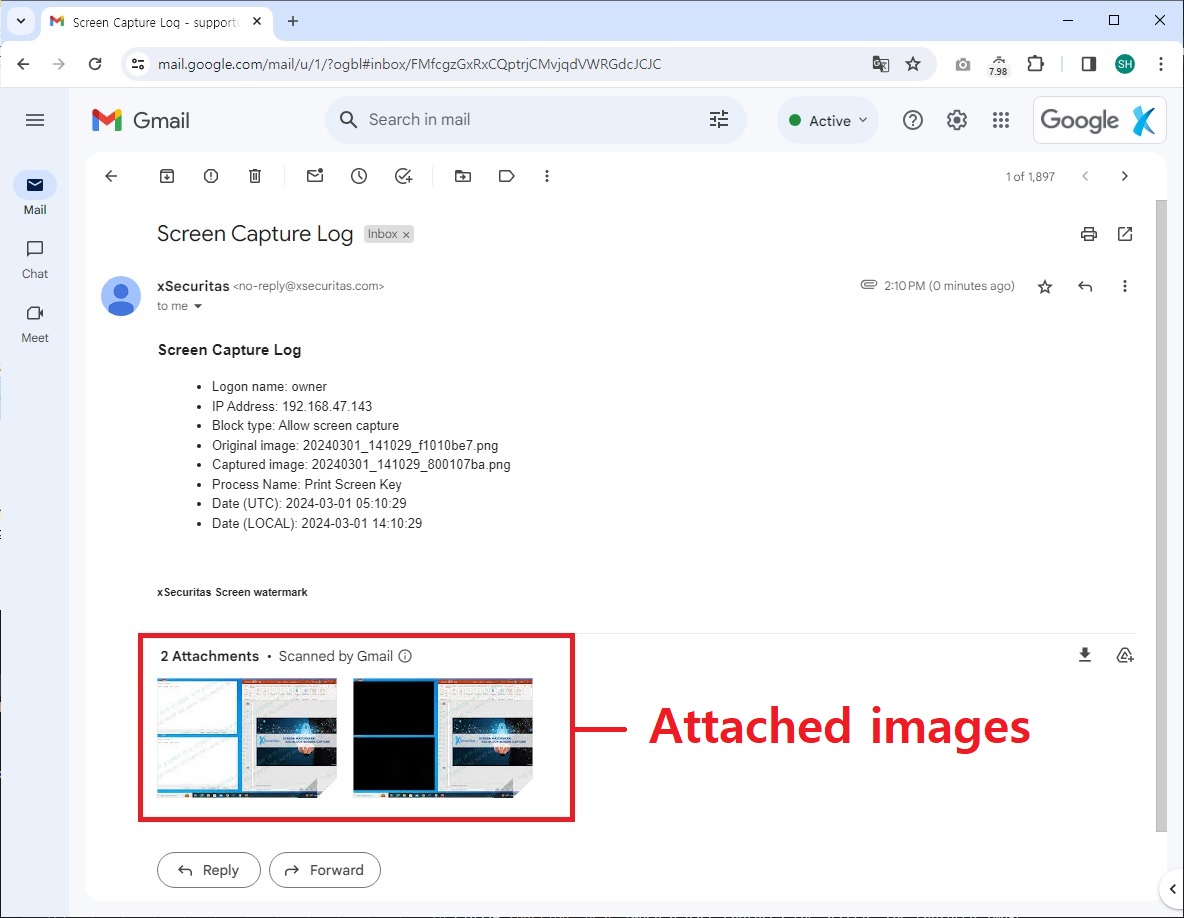
Example of a capture log sent to an administrator email
Flexibility according to environment

Depending on policy, the watermark might be hidden when the PC is used within the company, and visible when the PC is used outside the company. (Of course, you can display different watermarks when using a PC at work or at home.)
Depending on the environment, such as ICMP access, IP address, and local/remote connection, a different watermark may or may not be displayed on the user's PC.
Provides various functions
-
Policy Server
We provide cloud or on-premises policy servers, and for on-premises, no internet connection is required.
In the policy server, you can create policies, control agents (quit agent/uninstall agent, etc.), and view logs.
The administrator creates watermark policies in order to be distributed to groups or users. You can create multiple watermark policies.
Policies can be assigned by user’s ID, IP-address, Active Directory security group, domain, and sub-domain.
You can apply the same policy to all users or assign each policy to each group or user.
Reservation policies are available.
Administrators can preview watermark policies before distributing them to users.
-
Agent
Automatically start agent at PC boot (automatically start agent even in safe mode)
If the agent loses connection to the server, the latest policy watermark is displayed.
The Agent can interact with the company environment to show or hide the watermarks. We provide an API for this.
We provides a policy that sets the watermark to be included in the captured image only when capturing the screen and does not display the watermark on the screen.
Multi-Session support: A screen watermark is displayed on the user session when the user is switching.
The agent program periodically queries the policy server to see if the policy has changed, and if it does, the changed policy is applied.
Users cannot uninstall the agent or disable automatic startup of the agent.
-
Supports various metadata watermarks
For a dynamic watermarking, we provide about 30 types of meta-text including user ID, local IP address, remote IP address, MAC, Active directory information, Microsoft Sensitivity Label (Data Classification), date time and computer environment.
Supports text, images, and QR codes as watermarks.
You can specify various colors, position, transparency, angle, and number of text repetitions for the watermark.
Support for a wide range of operating systems
-
Windows
-
MacOS
-
Linux
-
Android
Frequently Asked Questions about xSecuritas Screen Watermark Enterprise
What is xSecuritas Enterprise Screen Watermark and how does it prevent screen-based data leakage?
xSecuritas Enterprise Screen Watermark overlays visible and invisible metadata watermarks and blocks screenshots or camera capture attempts, preventing unauthorized screen-based data leakage across Windows, macOS, Linux, and VDI environments.
How much CPU does the xSecuritas Screen Watermark Agent use?
Even with complex or high-density watermark configurations, the xSecuritas Agent typically uses 0–2% CPU, ensuring minimal system impact on Windows, macOS, and Linux environments.
Does the solution support invisible (forensic) watermarking?
Yes. xSecuritas embeds an encrypted invisible watermark inside captured images, enabling administrators to trace leaked screenshots back to specific users, devices, and sessions.
Which operating systems are supported by the Agent?
Windows 7/SP1+, Windows Server 2008 R2+, macOS 10.14+, and Linux distributions using glibc 2.17+ (Ubuntu, RedHat, CentOS, Debian, Fedora, OpenSUSE, KDE, etc.).
Does xSecuritas Screen Watermark work in VDI, RemoteApp, XenApp, Horizon, or Frame environments?
Yes. Watermarks render directly inside the remote session even when the user’s local PC does not have an Agent installed.
Does the solution block OS-level screenshot tools (PrintScreen, Snipping Tool, Win+Shift+S, etc.) and third-party screenshot apps?
Yes. The Agent blocks OS screenshot APIs and prevents or logs capture attempts from standard and third-party tools.
Can xSecuritas detect suspicious screen-capture behavior and generate logs?
Yes. All screenshot attempts, blocked captures, and protected content interactions are logged and uploaded to the Policy Server for analysis.
Does xSecuritas integrate with Microsoft Sensitivity Labels (MIP)?
Yes. Watermark visibility and behavior can be dynamically controlled based on Microsoft Information Protection (MIP) labels.
Can I show watermarks only for specific applications or websites?
Yes. You can configure allowlists/denylists so watermarks appear only on selected apps or URLs.
Does the Screen Watermark support multi-monitor and ultra-wide displays?
Yes. The Agent automatically detects monitor configuration, DPI scaling, and layout changes to render watermarks accurately.
What metadata can be displayed in the watermark?
More than 30 types, including user ID, PC name, IP/MAC address, AD attributes, date/time, session ID, QR code, and MIP label.
Does the Agent continue applying policies if the network is disconnected?
Yes. A secure local cache ensures the watermark remains active offline with the most recent policy.
Can the Policy Server assign policies by department, group, user, or IP range?
Yes. You can assign policies by AD OU, AD group, user ID, domain, IP address, or custom mapping rules.
Does xSecuritas support print watermarking and print control?
Yes. print Watermark inserts visible watermarks based on printer, app, sensitivity label, or user policy.
Does it support webcam watermarking and webcam blocking?
Yes. Webcam watermarks can be applied to live video streams, and webcam access can be restricted by app or website.
Can administrators remotely uninstall or disable Agents?
Yes. With proper permissions, administrators can remotely uninstall, quit, or restart Agents from the Policy Server.
How does the product detect and block unauthorized screen-capture tools?
The Agent intercepts Win32 APIs, DirectX layers, and known tool signatures to block or log unauthorized capture attempts.
Does watermarking work only inside RemoteApp windows without affecting the user’s local desktop?
Yes. Watermarks render specifically within the RemoteApp session window.
Does the solution work without an Internet connection?
Yes. On-premise deployments enable complete offline operation.
Can external contractors or temporary users receive different watermark policies?
Yes. Policies can be dynamically assigned by IP, AD group, domain, device type, or location.
Are screenshot, print, and webcam events stored centrally for auditing?
Yes. All security events are uploaded to the Policy Server and can be searched by user, device, time, or policy.
Does xSecuritas support deep forensic tracking?
Yes. Invisible watermarks + log correlation enable full-screen leakage tracing even for externally leaked images.
Can policies be scheduled or time-based?
Yes. Policies can be configured by time, department, user shifts, or reservation schedules.
Is real-time watermark preview available?
Yes. Administrators can preview watermark appearance directly in the Policy Server.
Does the Agent support automatic updates?
Yes. Windows, macOS, and Linux Agents support secure password-free auto-updates.
Can the Agent be deployed through SCCM, Intune, JAMF, GPO, PDQ, or MDM tools?
Yes. All major enterprise deployment frameworks are supported.
Does the Agent support hidden/stealth mode?
Yes. The tray icon can be hidden, and the Agent can operate in tamper-proof mode.
How does the Policy Server communicate with Agents?
Agents securely pull the latest policies from the server and batch-upload logs using encrypted communication channels.
Does the solution support multi-policy and multi-tenant environments?
Yes. Multiple policies can be created and automatically mapped to organizations, departments, or user groups.
Does the watermark require modifying our applications?
No. Watermark rendering operates independently of application code and requires no modification.
Do the Policy Server and Database Server need to run on the same machine?
They can run on the same server for small or mid-sized deployments. For environments with over 1,000 users, we recommend separating the Policy Server and Database Server for optimal performance and scalability.
Which database systems are supported by xSecuritas products?
xSecuritas solutions support MariaDB and Microsoft SQL Server (MS-SQL) as the primary databases for the Policy Server and logging system. Both databases are fully compatible with high-availability (HA) deployments and enterprise-scale environments.
Does xSecuritas support High Availability (HA) for enterprise environments?
Yes. Both the Database Server (MariaDB / MS-SQL) and the Web-based Policy Server can be fully configured in High Availability (HA) mode for fault-tolerant, mission-critical environments.
How does xSecuritas handle issues or incidents reported during product operation?
All reported issues are treated with the highest priority. Most problems are analyzed and patched within 1–2 business days. For more complex cases requiring additional time, xSecuritas provides customers with an estimated resolution date and continues to deliver progress updates until the issue is fully resolved.
Is xSecuritas certified for enterprise compliance such as ISO and SOC2?
Yes. xSecuritas is certified with ISO 27001:2022 and SOC 2 Type II.